Microsoft Office 2024

Microsoft Office 2024 is the latest version of MS Office.
Office 2024 for consumers launched on October 1, 2024, and it comes in two editions.
- Office 2024 Home – Includes Word, PowerPoint, Excel, and OneNote – $149.99
- Office 2024 Home & Business – Includes the above plus Outlook, as well as rights to use the apps in commercial environments – $249.99
More details: https://www.microsoft.com/en-us/microsoft-365/p/office-home-2024/cfq7ttc0pqvj
On the other hand, Microsoft Office 2021 (third release codenamed Office 16) is a version of the Microsoft Office suite of applications for the Microsoft Windows and macOS operating systems.
The most commonly used version of Microsoft Office in the US (and worldwide) is typically Microsoft Office 365.
As of August 2023, Microsoft Office 2016 and Microsoft Office 365 (now known as Microsoft 365) are among the most widely used versions in corporate environments.
- Microsoft 365: This subscription-based service offers the latest features, regular updates, and cloud integration, making it very popular for businesses that prioritize collaboration and remote work.
- Microsoft Office 2016: Many organizations still use this version due to its stability and the fact that it’s a one-time purchase, which can be more budget-friendly for some companies.
While newer versions like Office 2019 and Office 2021 exist, the widespread adoption of Microsoft 365 has shifted many organizations toward subscription models for their flexibility and continuous updates.
Security Issues with Microsoft 365:
https://blog.admindroid.com/top-15-vulnerabilities-in-microsoft-365/
As adversaries continue to target Microsoft 365 environments, it’s important to be aware of common security concerns — and understand what you can to protect your organization.
Learn about five common Office 365 security issues:
- Privilege Escalation
Privilege escalation is a common attack technique in which a threat actor attempts to elevate permissions — ideally to domain administrator — to launch attacks. To do this, adversaries can use legitimate tools already in an environment to evade detection from most antivirus and endpoint detection and response (EDR) software, a technique called living off the land. For example, threat actors can use Scheduled Task, a built-in functionality in Windows, to escalate their level of privilege.
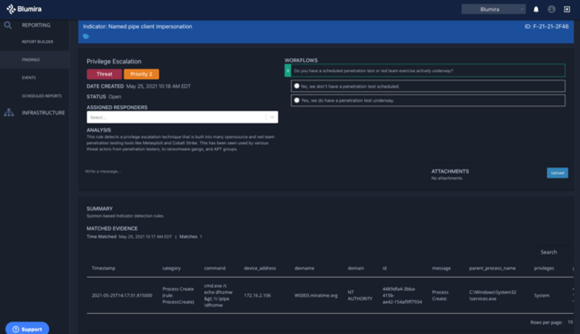
Fig. 1. – Blumira Finding – Privilege Escalation
Privilege escalation was the most popular type of Microsoft vulnerability in 2021 according to a BeyondTrust report, with nearly three times more than the previous year. In January 2021, CISA reported the Russia-based advanced persistent threat (APT) actor behind SolarWinds using privileged access in Microsoft 365 environments.
It’s important to be able detect suspicious activity associated with privilege escalation, such as creating inbox rules or external email forwarding rules.
How To Detect Email Forwarding Rules:
Bypassing Multi-factor Authentication
Multi-factor authentication (MFA) is a built-in security feature of all Microsoft 365 editions, but threat actors commonly circumvent those controls. Legacy authentication protocols such as IMAP/POP3 don’t support MFA, so threat actors can circumvent MFA when victims fail to restrict legacy authentication.
Another way is to use social engineering to change a victim’s registered phone number so that attackers receive the authentication text message. Adversaries can also circumvent MFA using OAuth, the authorization feature that allows users to sign in using Google or Facebook instead of creating a new account.
- No matter what method an attacker may use, it’s crucial to be able to detect when MFA is disabled on a Microsoft 365 account.
Phishing
Phishing, when a threat actor sends emails disguised as legitimate companies to obtain information, is the top attack vector for ransomware. And Microsoft is the most impersonated brand, according to Barracuda’s report.
Phishing is often the one of the first actions an attacker will take to gain initial access into an environment. Phishing emails usually prompt the victim to click on a malicious link or attachment that may execute code, run a command, or give consent to access their mailbox.
Microsoft 365 has an email protection feature that can detect and neutralize phishing campaigns — but it can only go so far. It doesn’t actively scan all email content, and the Safe Attachments feature detects malware using sandboxing rather than with more sophisticated methods.
- To prevent phishing, it’s important to apply additional layers of email security and be able to detect suspicious email sending patterns.
